Market Trends
Key Emerging Trends in the Breach Attack Simulation Market
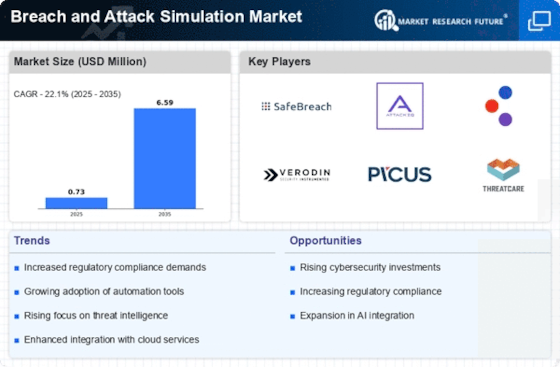
The BAS industry has become increasingly important as businesses realize how important it is to strengthen their digital defenses. An important trend in the industry is the increasing use of BAS solutions in several sectors of the economy. Businesses are being more aggressive at mimicking actual cyberattacks to find holes and weak points in their security framework. The knowledge that more sophisticated and quickly changing threats may require more than traditional, reactive methods is what is driving this move in cybersecurity toward proactive measures.
This market trend is primarily being driven by the necessity for enterprises to proactively assess their security posture and the increasing sophistication of cyber threats. In the market, cloud-based BAS solutions have also grown in popularity. Security solutions that are flexible enough to adjust to changing cloud environments are essential as more and more businesses move their activities to the cloud. Scalability, flexibility, and real-time insights are features that make cloud-based BAS systems appealing to companies trying to protect their digital assets in a variety of dynamic environments.
The regulatory environment is a key element influencing market movements in BAS. Organizations are subject to strict cybersecurity regulations from governments and regulatory authorities across the globe to safeguard confidential information and protect people's privacy. Due to this, companies are now investing in BAS and other cutting-edge security solutions to abide by the legislation and prevent the dire repercussions of data breaches. Growing competition amongst solution providers in the BAS industry is spurring innovation and the creation of more advanced technologies. The vendors prioritize improving the user experience, streamlining the deployment procedures, and providing all-inclusive solutions that address an extensive variety of cyberthreats. BAS solutions are changing as a result of this rivalry to better serve the varied needs of businesses across various industries.
Furthermore, market trends are shaped by the incorporation of AI and ML technologies into BAS solutions. Through the automation of vulnerability identification, the analysis of intricate information, and the provision of valuable insights, these cutting-edge technologies improve the effectiveness of BAS. Organizations can quickly eliminate possible risks by reducing response times and improving threat detection accuracy with the integration of AI and ML.














Leave a Comment