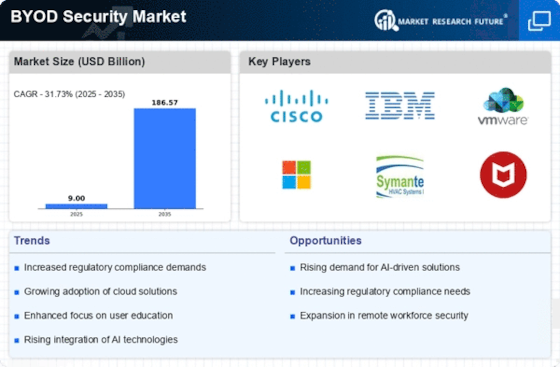
Top Industry Leaders in the BYOD Security Market

BYOD Security Market: Dive into the Latest News and Updates
The "Bring Your Own Device Security" (BYOD) trend has transformed workspaces, allowing employees to use personal devices for work tasks. However, this convenience comes with security challenges, requiring robust solutions to protect corporate data and networks.
Some of BYOD Security Companies Listed Below:
- International Business Machines Corporation (U.S.)
- Citrix Systems, Inc. (U.S.)
- Good Technology Corporation. (U.S.)
- Mobileiron Inc. (U.S.)
- VMware, Inc. (U.S.)
- Fortinet Inc. (U.S.)
- Cisco Systems (U.S.)
- Avaya Inc. (U.S.)
- Hewlett Packard Enterprise (U.S.)
- Symantec Corporation (U.S.)
Strategies Fueling Growth:
-
Focus on Data Security and Compliance: Providing robust data encryption, containerization technologies, and data loss prevention solutions protects sensitive information and ensures compliance with industry regulations. -
User Centric Approach and Secure Access: Offering user-friendly BYOD solutions with easy device enrollment, single sign-on, and secure access controls enhances user experience while maintaining security. -
Cloud-Based and Scalable Solutions: Cloud-based BYOD platforms offer centralized management, flexible deployment options, and lower upfront costs, catering to diverse organizational needs and future growth. -
Integration with Existing IT Infrastructure: BYOD solutions that seamlessly integrate with existing IT management tools, security platforms, and directory services streamline operations and simplify administration.
Market Share Decoding: Key Factors to Consider:
-
Product Portfolio Breadth and Functionality: Providers with diverse BYOD security features, including device management, data encryption, app control, and network access control, cater to broader needs and attract larger customer bases. -
Industry Expertise and Compliance Focus: Companies with deep understanding of specific industries and their compliance requirements can tailor BYOD solutions for optimal security within those sectors, gaining an edge in niche markets. -
Cloud-Based Deployment and Scalability: BYOD platforms offering flexible cloud deployment models, easy upgrades, and the ability to handle large device deployments adapt to diverse organizational needs and future growth. -
User Experience and Ease of Management: User-friendly interfaces, intuitive enrollment processes, and simple device management tools ensure user adoption and reduce administrative burden for IT teams.
New and Emerging Stars: Illuminating the BYOD Path:
-
Zero-Trust Security and Context-Aware Access: Startups like Zscaler and Okta implement zero-trust security models for BYOD, granting access based on device posture, user context, and real-time risk assessments, minimizing attack surfaces. -
AI-Powered Threat Detection and Behavioral Analysis: Companies like Deepwatch and Darktrace integrate AI into BYOD security, enabling real-time anomaly detection, suspicious activity identification, and proactive threat mitigation for BYOD devices. -
Blockchain-Based Secure Device Identities and Attestation: Startups like Evernym and Civic explore blockchain technology for secure device identities, tamper-proof device configuration records, and decentralized authentication protocols, enhancing trust and accountability in BYOD environments.
Latest Company Updates:
October 26, 2023:
-
Focus on containerization: Containerization technologies isolate corporate data and applications on employees' devices, enhancing security and control.
November 18, 2023:
-
Survey reveals 74% of organizations allow BYOD, but only 42% feel confident in their security measures: This highlights the gap between adoption and effective security implementation. -
Focus on zero-trust access: Implementing zero-trust principles ensures continuous verification and access control regardless of device or location.
December 6, 2023:
-
Apple releases iOS 17 with enhanced security features for BYOD devices: These include app sandboxing improvements and stricter data access controls. -
Focus on phishing and malware threats: Cybercriminals actively target BYOD devices through social engineering and malicious apps.
January 9, 2024:
-
AI and machine learning (ML) integration for anomaly detection and threat prevention: Advanced algorithms can identify suspicious activity on BYOD devices in real-time. -
Focus on user education and awareness: Empowering employees with cybersecurity knowledge and best practices is key to minimizing risks.
January 10, 2024:
-
BYOD policies evolve to address data privacy concerns: Companies are updating policies to ensure compliance with regulations and protect employee data. -
Focus on endpoint security solutions: Comprehensive endpoint security software strengthens BYOD device protection through data encryption, malware detection, and remote management.