Market Trends
Key Emerging Trends in the Security Software Telecom Market
The telecom industry is undergoing rapid evolution, driven by the increasing reliance on digital technologies and the growing threat landscape. Security software has become an indispensable component of telecom networks, as providers seek to safeguard sensitive data and protect against cyber threats. One of the prominent trends in the security software telecom market is the rising demand for comprehensive and integrated solutions. With the proliferation of connected devices and the expansion of network infrastructure, telecom operators are looking for holistic security solutions that can address a wide range of threats across their networks. Integrated security platforms that combine features such as firewall protection, intrusion detection, and threat intelligence are gaining traction as operators seek to simplify their security infrastructure and improve overall efficiency.
Another notable trend is the emphasis on cloud-based security solutions. As telecom networks become increasingly virtualized and software-defined, there is a growing need for security solutions that can scale dynamically and adapt to changing network conditions. Cloud-based security offerings provide flexibility and scalability, allowing telecom operators to deploy and manage security services more effectively while reducing the need for on-premises hardware and infrastructure. Additionally, cloud-based solutions offer advanced threat detection and response capabilities, leveraging machine learning and AI algorithms to detect and mitigate emerging threats in real-time.
Furthermore, there is a growing focus on proactive threat intelligence and analytics in the security software telecom market. Telecom operators are investing in advanced analytics platforms that can analyze vast amounts of network data to identify potential security threats and vulnerabilities. By leveraging big data analytics and machine learning algorithms, operators can gain deeper insights into network behavior and detect anomalous activities indicative of cyber attacks or security breaches. Proactive threat intelligence enables operators to take preemptive action to mitigate risks and protect their networks from evolving threats.
Additionally, the convergence of security and networking technologies is driving innovation in the security software telecom market. With the rise of software-defined networking (SDN) and network functions virtualization (NFV), telecom operators are increasingly integrating security features directly into their network infrastructure. This trend, known as security-driven networking, enables operators to embed security capabilities such as encryption, access control, and traffic filtering directly into the network fabric, providing enhanced protection against cyber threats while minimizing latency and overhead.
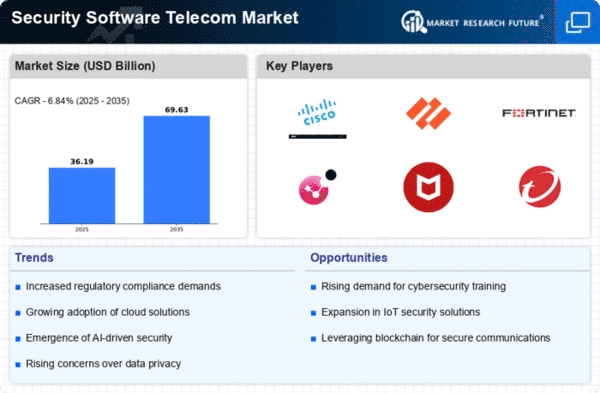
Moreover, there is a growing emphasis on regulatory compliance and data privacy in the security software telecom market. With the implementation of stringent data protection regulations such as GDPR and CCPA, telecom operators are under increasing pressure to ensure the confidentiality, integrity, and availability of customer data. Security software solutions that offer robust compliance management and data encryption capabilities are in high demand as operators seek to demonstrate compliance with regulatory requirements and protect sensitive customer information from unauthorized access or disclosure.
Furthermore, the proliferation of 5G networks is driving demand for security software solutions tailored to the unique challenges of next-generation telecom infrastructure. With 5G enabling new use cases such as IoT, edge computing, and mission-critical applications, operators are facing unprecedented security risks and complexities. Security software vendors are developing specialized solutions designed to secure 5G networks against emerging threats such as network slicing attacks, device vulnerabilities, and traffic interception. These solutions leverage advanced encryption, authentication, and access control mechanisms to safeguard 5G infrastructure and ensure the integrity and confidentiality of data transmitted over these networks.
















Leave a Comment