Rise of Remote Work Culture
The rise of remote work culture in Canada is significantly impacting the mobile user-authentication market. As more organizations adopt flexible work arrangements, the need for secure remote access to corporate resources has become essential. This shift has led to an increased reliance on mobile user-authentication solutions to ensure that only authorized personnel can access sensitive information from various locations. In 2025, it is estimated that over 40% of Canadian employees will work remotely at least part-time, creating a substantial demand for secure authentication methods. Consequently, businesses are likely to invest in mobile user-authentication technologies that facilitate secure remote access, thereby driving growth in the market.
Consumer Demand for Convenience
In the mobile user-authentication market, consumer preferences are shifting towards convenience and seamless user experiences. As mobile devices become integral to daily life, users increasingly favor authentication methods that are quick and easy to use. A recent survey indicated that over 70% of Canadian consumers prefer biometric authentication methods, such as fingerprint or facial recognition, due to their speed and ease of use. This growing demand for user-friendly solutions is likely to encourage developers to innovate and enhance mobile user-authentication technologies. Consequently, businesses that prioritize convenience in their authentication processes may gain a competitive edge, further propelling the growth of the mobile user-authentication market.
Increasing Cybersecurity Threats
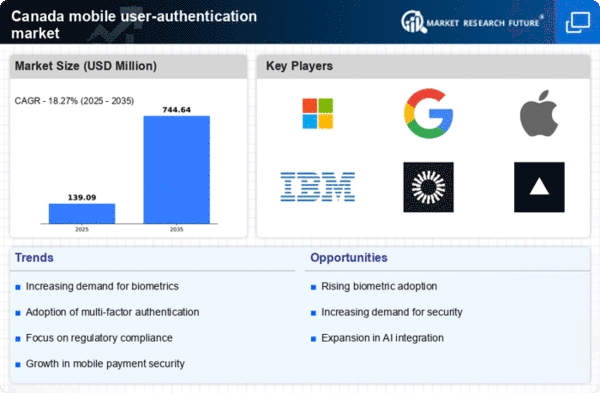
The mobile user-authentication market is experiencing heightened demand. This demand is due to the increasing frequency and sophistication of cyber threats in Canada. As organizations face a growing number of data breaches and identity theft incidents, the need for robust authentication solutions becomes paramount. In 2025, it is estimated that cybercrime could cost Canadian businesses over $10 billion annually, prompting a shift towards more secure authentication methods. This trend is likely to drive investments in mobile user-authentication technologies, as companies seek to protect sensitive information and maintain customer trust. The urgency to mitigate risks associated with unauthorized access is propelling the adoption of advanced authentication solutions, thereby shaping the mobile user-authentication market landscape.
Advancements in Mobile Technology
The rapid advancements in mobile technology are significantly influencing the mobile user-authentication market. With the proliferation of smartphones and tablets, the capabilities of mobile devices have expanded, enabling more sophisticated authentication methods. In 2025, it is projected that over 90% of Canadians will own a smartphone, creating a vast user base for mobile authentication solutions. This technological evolution allows for the integration of advanced features such as biometric sensors and artificial intelligence, enhancing security and user experience. As mobile technology continues to evolve, the mobile user-authentication market is likely to witness increased adoption of innovative solutions that leverage these advancements.
Regulatory Pressures for Enhanced Security
The mobile user-authentication market is shaped by regulatory pressures. These pressures aim to enhance security measures across various sectors in Canada. Government regulations, such as the Personal Information Protection and Electronic Documents Act (PIPEDA), mandate organizations to implement stringent security protocols to protect consumer data. As compliance becomes a critical concern, businesses are increasingly investing in mobile user-authentication solutions to meet these regulatory requirements. The need to avoid hefty fines and reputational damage is driving organizations to adopt more secure authentication methods, thereby fostering growth in the mobile user-authentication market. This trend indicates a strong alignment between regulatory compliance and the adoption of advanced authentication technologies.















Leave a Comment