Rising Cybersecurity Threats
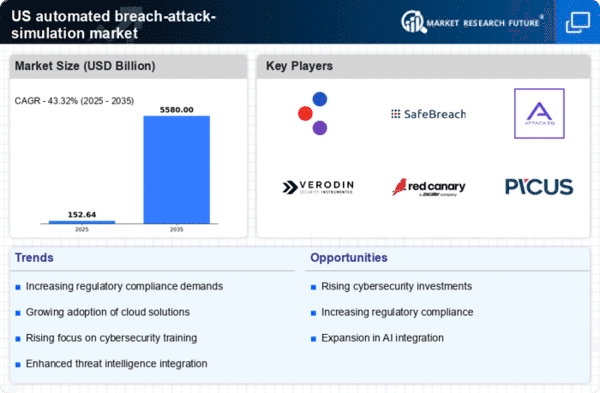
The increasing frequency and sophistication of cyberattacks is a primary driver for the automated breach-attack-simulation market. Organizations are facing a growing array of threats, including ransomware, phishing, and advanced persistent threats (APTs). In response, companies are investing heavily in cybersecurity measures, with the market projected to reach $300 billion by 2025. This heightened awareness of vulnerabilities compels businesses to adopt automated breach-attack simulations to proactively identify and mitigate risks. By simulating real-world attack scenarios, organizations can better prepare their defenses, thereby enhancing their overall security posture. The urgency to protect sensitive data and maintain customer trust further fuels the demand for these solutions, making it a critical component of modern cybersecurity strategies.
Increased Regulatory Pressures
Regulatory compliance is becoming increasingly stringent, driving the demand for the automated breach-attack-simulation market. Organizations are required to adhere to various regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Non-compliance can result in hefty fines, which can reach up to 4% of annual global revenue. As a result, businesses are turning to automated breach-attack simulations to ensure they meet compliance requirements and avoid potential penalties. These simulations help organizations identify gaps in their security frameworks and demonstrate due diligence to regulators. The need for compliance not only protects organizations from financial repercussions but also enhances their reputation in the marketplace, making this driver particularly influential.
Growing Awareness of Security Posture
There is a notable increase in awareness regarding the importance of a robust security posture among organizations, which is propelling the automated breach-attack-simulation market. Companies are recognizing that traditional security measures may not be sufficient to combat evolving threats. As a result, they are investing in advanced security solutions, with the market expected to grow at a CAGR of 20% through 2025. Automated breach-attack simulations provide organizations with insights into their vulnerabilities and the effectiveness of their security measures. This proactive approach allows businesses to strengthen their defenses and reduce the likelihood of successful attacks. The growing emphasis on security culture within organizations further underscores the relevance of this market driver.
Technological Advancements in Cybersecurity
Technological advancements are significantly influencing the automated breach-attack-simulation market. Innovations in artificial intelligence (AI) and machine learning (ML) are enhancing the capabilities of these simulations, allowing for more realistic and comprehensive assessments of security vulnerabilities. The integration of AI-driven analytics can improve threat detection and response times, making organizations more resilient against attacks. As technology continues to evolve, the market is expected to witness a surge in demand for sophisticated simulation tools that can adapt to new threats. This trend indicates a shift towards more dynamic and responsive cybersecurity strategies, positioning automated breach-attack simulations as essential tools for modern organizations.
Increased Investment in Cybersecurity Solutions
The surge in investment in cybersecurity solutions is a significant driver for the automated breach-attack-simulation market. Organizations are allocating larger portions of their budgets to cybersecurity, with spending projected to exceed $200 billion by 2025. This trend is fueled by the recognition of cybersecurity as a critical business priority. Automated breach-attack simulations are increasingly viewed as essential components of a comprehensive cybersecurity strategy, enabling organizations to test their defenses against potential breaches. The willingness to invest in these solutions reflects a broader understanding of the financial and reputational risks associated with cyber threats. As businesses continue to prioritize cybersecurity, the demand for automated breach-attack simulations is likely to grow.