Increased Regulatory Pressure
The breach attack-simulation market is also driven by increased regulatory pressure on organizations to comply with cybersecurity standards. Governments in the GCC are implementing stricter regulations to protect sensitive data and ensure the security of critical infrastructure. In 2025, it is anticipated that compliance-related spending will exceed $20 billion in the region. This regulatory environment compels organizations to adopt breach attack-simulation solutions to demonstrate compliance and mitigate risks associated with non-compliance. By investing in these simulations, businesses can proactively identify weaknesses in their security frameworks and align their practices with regulatory requirements.
Rising Cyber Threat Landscape
The breach attack-simulation market is experiencing growth due to the escalating cyber threat landscape in the GCC region. Organizations are increasingly aware of the potential risks posed by cybercriminals, which has led to a heightened demand for proactive security measures. In 2025, it is estimated that cybercrime costs could reach $10 trillion globally, prompting businesses to invest in breach attack-simulation solutions. These tools allow organizations to simulate attacks and identify vulnerabilities before they can be exploited. As a result, companies are prioritizing investments in breach attack-simulation technologies to enhance their security posture and protect sensitive data.
Growing Awareness of Data Privacy
The breach attack-simulation market is significantly influenced by the growing awareness of data privacy among consumers and businesses in the GCC. With increasing incidents of data breaches, organizations are compelled to adopt robust security measures to safeguard personal information. In 2025, it is projected that the data protection market will reach $150 billion, indicating a strong focus on compliance and risk management. This trend drives the demand for breach attack-simulation solutions, as they help organizations assess their security frameworks and ensure adherence to data protection regulations. Consequently, businesses are investing in these simulations to build trust with customers and mitigate potential legal repercussions.
Shift Towards Proactive Security Measures
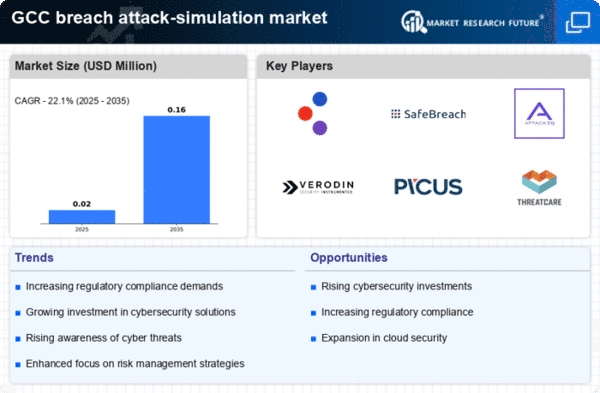
The breach attack-simulation market is witnessing a shift towards proactive security measures as organizations recognize the limitations of traditional reactive approaches. In the GCC, businesses are increasingly adopting a proactive stance by utilizing breach attack-simulation tools to identify vulnerabilities before they can be exploited. This shift is reflected in the growing market, which is projected to expand at a CAGR of 25% from 2025 to 2030. By simulating potential attacks, organizations can better prepare for real-world threats and enhance their incident response capabilities. This proactive approach not only strengthens security but also fosters a culture of continuous improvement in cybersecurity practices.
Technological Advancements in Security Solutions
The breach attack-simulation market is benefiting from rapid technological advancements in security solutions. Innovations such as artificial intelligence (AI) and machine learning (ML) are being integrated into breach attack-simulation tools, enhancing their effectiveness in identifying vulnerabilities. In 2025, the AI in cybersecurity market is expected to reach $38 billion, reflecting the growing reliance on advanced technologies. These advancements enable organizations to conduct more realistic simulations, providing deeper insights into potential attack vectors. As a result, businesses in the GCC are increasingly adopting breach attack-simulation solutions to stay ahead of evolving cyber threats and improve their overall security strategies.